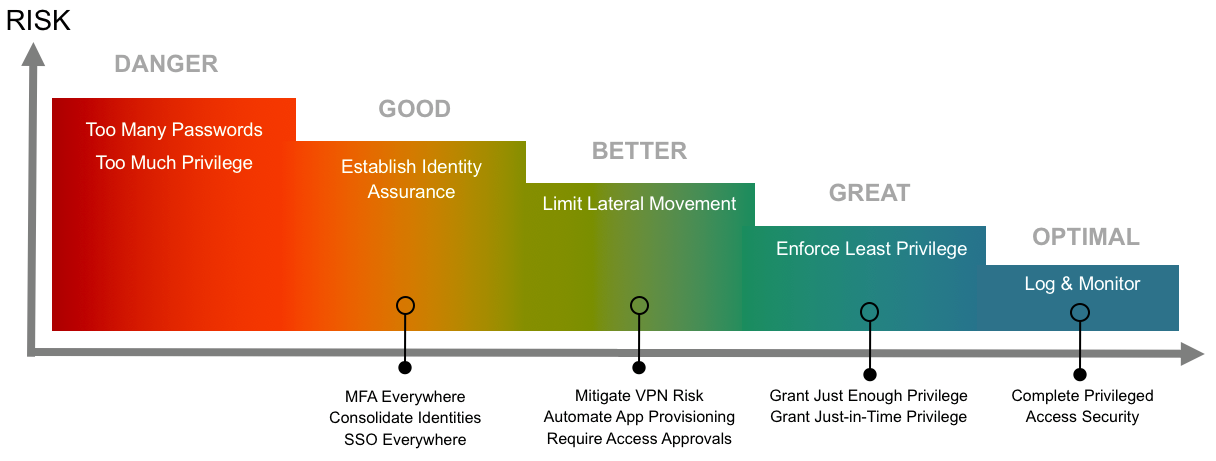
RETHINK and Challenge the Perimeter-Based Approach
Cybercriminals are breaching systems through compromised credentials, primarily weak passwords. The perimeter-based approach only protects endpoints, firewalls, and networks. It overlooks the vulnerability of identities and passwords. This approach is outdated and requires rethinking, especially when considering Privileged Identity Management Solutions.
REDEFINE Security to Follow Identity
The hybrid enterprise is boundaryless, with millions of connections both inside and outside your organisation. Protect identities as they access apps, devices, and infrastructure, whether on-premises or in the cloud. These identities are crucial to securing your enterprise. Security must shift from perimeter-based to identity-centric, including Privileged Identity Management Solutions.
ADAPT as the Boundaryless Landscape Evolves
Cyber threats are growing more sophisticated, and static security methods cannot keep up with today’s changing landscape. Traditional perimeter-based security is no longer enough. Your security must adapt as cloud, mobile, and IoT technologies expand. Privileged Identity Management Solutions offer seamless protection that evolves with your enterprise.
STOP the Breach with the Power of Identity Services
Centrify provisions user accounts, manages access, and records activity. It offers context-aware controls to authorise access securely. Centrify protects apps and infrastructure for all users, anywhere, on any device. By securing identities with Privileged Identity Management Solutions, businesses prevent breaches before they happen.